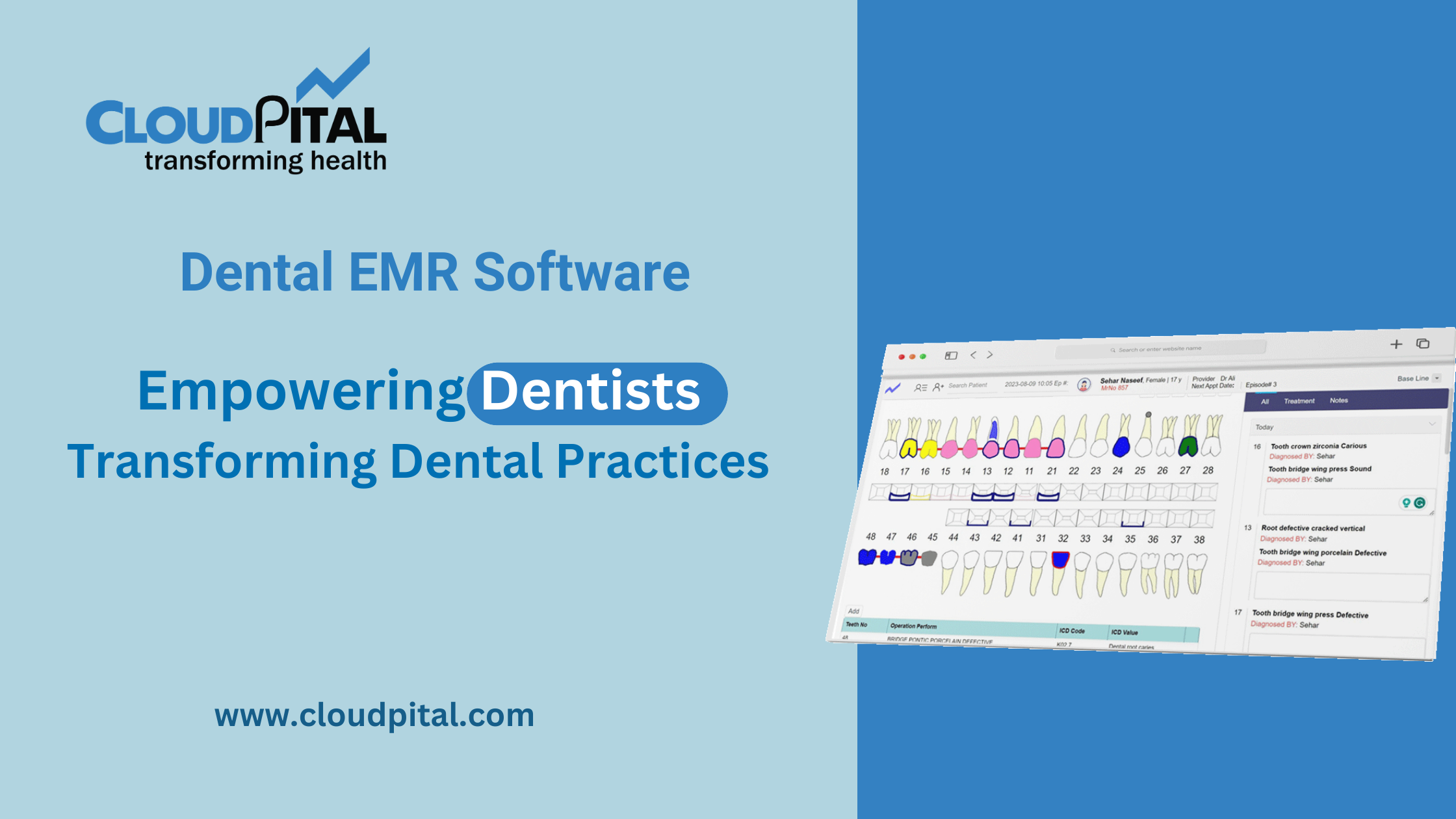
Cloudpital # 1 is one of the top EMR Software in Saudi Arabia has revolutionized the healthcare industry by enabling the efficient management of patient data. In Saudi Arabia, where healthcare systems are rapidly evolving, ensuring the security of patient data has become a top priority. As healthcare providers increasingly rely on digital platforms to store and manage sensitive information, EMR software is playing a critical role in safeguarding patient data. This article explores how EMR software enhances patient data security in Saudi Arabia, focusing on key features such as encryption, access controls, compliance with regulations, and more.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
Email: sales@cloudpital.com
Cloudpital # 1 EMR Software in Saudi Arabia

Data Encryption
Data encryption is a fundamental feature of EMR Software in Saudi Arabia that enhances patient data security. In Saudi Arabia, healthcare providers must comply with strict regulations that mandate the protection of patient data, and encryption is a key tool in meeting these requirements.
- Encryption of Data at Rest: EMR software in Saudi Arabia encrypts patient data stored within the system (data at rest). This means that even if unauthorized individuals gain access to the storage system, the data remains unreadable without the proper decryption key. This encryption ensures that patient information is protected from potential breaches.
- Encryption of Data in Transit: EMR systems also encrypt data when it is being transmitted between systems (data in transit). Whether the data is being sent to another healthcare provider, a patient, or an external system, encryption ensures that the information cannot be intercepted or tampered with during transmission.
- Advanced Encryption Standards: In Saudi Arabia, EMR software typically employs advanced encryption standards (AES) to secure patient data. AES is widely recognized for its strength and effectiveness in protecting sensitive information, making it a trusted choice for healthcare organizations.
Access Controls and Authentication
Access controls are another critical feature of EMR software that enhances patient data security. These controls ensure that only authorized personnel can access patient information, reducing the risk of unauthorized access and data breaches.
- Role-Based Access Control (RBAC): EMR systems in Saudi Arabia often use Role-Based Access Control (RBAC) to manage access to patient data. RBAC assigns access rights based on the roles of individuals within the healthcare organization. For example, a doctor may have access to full patient records, while administrative staff may only have access to billing information. This ensures that sensitive data is only accessible to those who need it to perform their duties.
- Multi-Factor Authentication (MFA): To enhance security further, EMR software often incorporates Multi-Factor Authentication (MFA). MFA requires users to provide two or more forms of identification before accessing patient data. This could include something the user knows (e.g., a password), something the user has (e.g., a security token), or something the user is (e.g., a fingerprint). MFA adds an additional layer of security, making it more difficult for unauthorized individuals to gain access.
- Audit Trails and Monitoring: EMR software in Saudi Arabia includes audit trails that track all access and actions taken within the system. These audit trails provide a detailed record of who accessed patient data, when it was accessed, and what actions were taken. Regular monitoring of these audit trails helps identify and respond to any suspicious activity.
Compliance with Saudi Arabian Healthcare Regulations
In Saudi Arabia, healthcare providers must comply with strict regulations regarding the handling of patient data. EMR software is designed to meet these regulatory requirements, ensuring that patient data is handled securely and in accordance with the law.
- Saudi Ministry of Health (MOH) Standards: The Saudi Ministry of Health has established specific standards and guidelines for the protection of patient data. EMR software used in Saudi Arabia is designed to comply with these standards, ensuring that healthcare providers meet their legal obligations regarding data security.
- Compliance with National Cybersecurity Authority (NCA) Guidelines: The National Cybersecurity Authority (NCA) in Saudi Arabia has issued guidelines to protect critical national infrastructure, including healthcare systems. EMR Software in Saudi Arabia incorporates these guidelines to enhance the security of patient data, ensuring that it is protected against cyber threats and breaches.
- Data Privacy Regulations: Saudi Arabia has implemented data privacy regulations that require healthcare providers to protect patient information from unauthorized access, disclosure, and misuse. EMR software ensures compliance with these regulations by incorporating robust security features and protocols that safeguard patient data.

Data Backup and Disaster Recovery
Data backup and disaster recovery are essential components of PMS in Saudi Arabia that contribute to patient data security. In the event of a system failure, natural disaster, or cyberattack, these features ensure that patient data remains secure and can be quickly restored.
- Regular Data Backups: EMR software in Saudi Arabia is configured to perform regular backups of patient data. These backups are stored in secure locations, often in encrypted formats, ensuring that the data can be recovered in the event of a system failure or data loss. Regular backups are critical for maintaining data integrity and ensuring continuity of care.
- Disaster Recovery Plans: EMR systems include disaster recovery plans that outline the procedures for restoring patient data and system functionality following a disaster. These plans are designed to minimize downtime and ensure that healthcare providers can continue to access patient information, even in the face of unexpected events.
- Cloud-Based Storage Solutions: Many EMR systems in Saudi Arabia utilize cloud-based storage solutions for data backups. Cloud storage offers enhanced security features, including encryption, redundancy, and access controls, ensuring that patient data is protected even if local systems are compromised.
Interoperability and Secure Data Sharing
Interoperability and secure data sharing are key features of EMR software that enhance patient data security while enabling the exchange of information between healthcare providers.
- Interoperability Standards: EMR software in Saudi Arabia is designed to comply with international interoperability standards, such as Health Level Seven (HL7) and Fast Healthcare Interoperability Resources (FHIR). These standards ensure that patient data can be securely shared between different healthcare systems while maintaining its integrity and confidentiality.
- Secure Data Exchange Protocols: When patient data is shared between healthcare providers, EMR software employs secure data exchange protocols, such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS). These protocols encrypt the data during transmission, ensuring that it cannot be intercepted or accessed by unauthorized parties.
- Patient Consent Management: EMR systems in Saudi Arabia often include features that allow patients to control who has access to their data. Patients can provide or revoke consent for the sharing of their information, ensuring that their privacy preferences are respected. This feature enhances patient trust and ensures compliance with data protection regulations.
Training and Awareness Programs
While technology plays a critical role in securing patient data, the human element is equally important. EMR software enhances patient data security by supporting training and awareness programs for healthcare staff.
- User Training on Security Practices: EMR systems in Saudi Arabia often include training modules that educate healthcare staff on best practices for data security. This training covers topics such as password management, recognizing phishing attempts, and securely accessing patient data. By educating users, healthcare organizations can reduce the risk of data breaches caused by human error.
- Security Awareness Campaigns: Regular security awareness campaigns help keep data security top of mind for healthcare staff. These campaigns may include reminders about the importance of following security protocols, updates on emerging threats, and tips for protecting patient data.
- Incident Response Training: In addition to general security training, EMR software supports incident response training, ensuring that healthcare staff are prepared to respond to data breaches or other security incidents. This training helps minimize the impact of security breaches and ensures that appropriate actions are taken to protect patient data.
Data Anonymization and De-Identification
Data anonymization and de-identification are techniques used by EMR software to protect patient data, particularly when it is used for research or shared with external parties.
- Anonymization: EMR software in Saudi Arabia can anonymize patient data by removing or masking personally identifiable information (PII). Anonymized data cannot be traced back to an individual, making it a valuable tool for protecting patient privacy when data is used for research or analytics.
- De-Identification: In some cases, Medical Solutions in Saudi Arabia may use de-identification techniques to remove specific identifiers from patient data while retaining the ability to re-identify the data if necessary. De-identification strikes a balance between data utility and privacy, ensuring that patient information can be used responsibly.
- Compliance with Ethical Standards: The use of anonymization and de-identification techniques helps healthcare providers in Saudi Arabia comply with ethical standards and regulations regarding the use of patient data for research. By protecting patient privacy, EMR software supports the responsible use of health data.
Conclusion
EMR software plays a pivotal role in enhancing patient data security in Saudi Arabia, where the protection of sensitive health information is of paramount importance. Through features such as encryption, access controls, compliance with regulations, data backup, secure data sharing, and user training, EMR systems ensure that patient data is safeguarded against unauthorized access, breaches, and misuse. As the healthcare sector in Saudi Arabia continues to evolve, the ongoing development and implementation of robust EMR security measures will be essential in maintaining the trust of patients and ensuring the integrity of the healthcare system.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
Email: sales@cloudpital.com
EMR Software in Saudi Arabia
EMR Software in Saudi Arabia
EMR Software in Saudi Arabia
EMR Software in Saudi Arabia enhance patient data security similar software solutions prices were updated on 2025-06-30T22:21:03+00:00 in Saudi Arabia in Mecca, Medina, Riyadh, Khamis Mushait, Yanbu, Jeddah, Dammam, Unaizah, Uqair, Ha’il, Ta if, Al Bahah, Dhahran, King Abdullah Economic City, Najran, Diriyah, Qatif, Khafji, Jubail, Abqaiq, List of Cities and Towns in Saudi Arabia, Ras Tanura, Turubah, Jazan Economic City, Knowledge Economic City, Medina, Khobar, Abha, Tabuk, Saudi Arabia, similar software solutions prices were updated on 2025-06-30T22:21:03+00:00 We also provide in Saudi Arabia services solutions company in Hafar Al-Batin, Udhailiyah, Al-Awamiyah, Hofuf, Hautat Sudair, Buraidah, Tayma, Duba, ‘uyayna, Saihat, Al-Kharj, Al-ula, Jizan, Rumailah, Ar Rass, Arar, Shaybah, Al Majma’ah, Rabigh, Dhurma, Haradh, List of Saudi Cities by Gdp Per Capita, Badr, Sudair Industrial City, Baljurashi, Shaqraa, Al-Khutt, Habala, Ad Dawadimi, Dawadmi, Layla, similar software solutions prices were updated on 2025-06-30T22:21:03+00:00 Price is SAR 100 and this was updated on updated on 2025-06-30T22:21:03+00:00 similar EMR Software in Saudi Arabia enhance patient data security software solutions prices were updated on 2025-06-30T22:21:03+00:00 in Saudi Arabia in Haql, Afif, Al-Abwa, Farasan, Al-Jaroudiya, Thadig, Al-Thuqbah, Al Wajh, Almardmah, Al-Zilfi, Muzahmiyya, Prince Abdul Aziz Bin Mousaed Economic City, Tharmada’a, Skaka, Um Al-Sahek, Sharurah, Tanomah, Bisha, Dahaban, Al Qunfudhah, Qurayyat, Saudi Arabia, Ha’ir, as Sulayyil, Al Lith, Turaif, Al-Gway’iyyah, Samtah, Wadi Ad-Dawasir, Az Zaimah, Safwa City, Jalajil, Harmah, Mastoorah, Hotat Bani Tamim, Jabal Umm Al Ru’us, Rafha, Qaisumah, Al-Ghat, Hajrah, Al-Hareeq. Excerpt: Jeddah (also spelled Jiddah, Jidda, or Jedda; Arabic: Jidda) is a Saudi Arabian city located on the coast of the Red Sea and is the major urban center of western Saudi Arabia similar software solutions prices were updated on 2025-06-30T22:21:03+00:00 Price is SAR 100 and this was updated on updated on 2025-06-30T22:21:03+00:00
13-8-2024