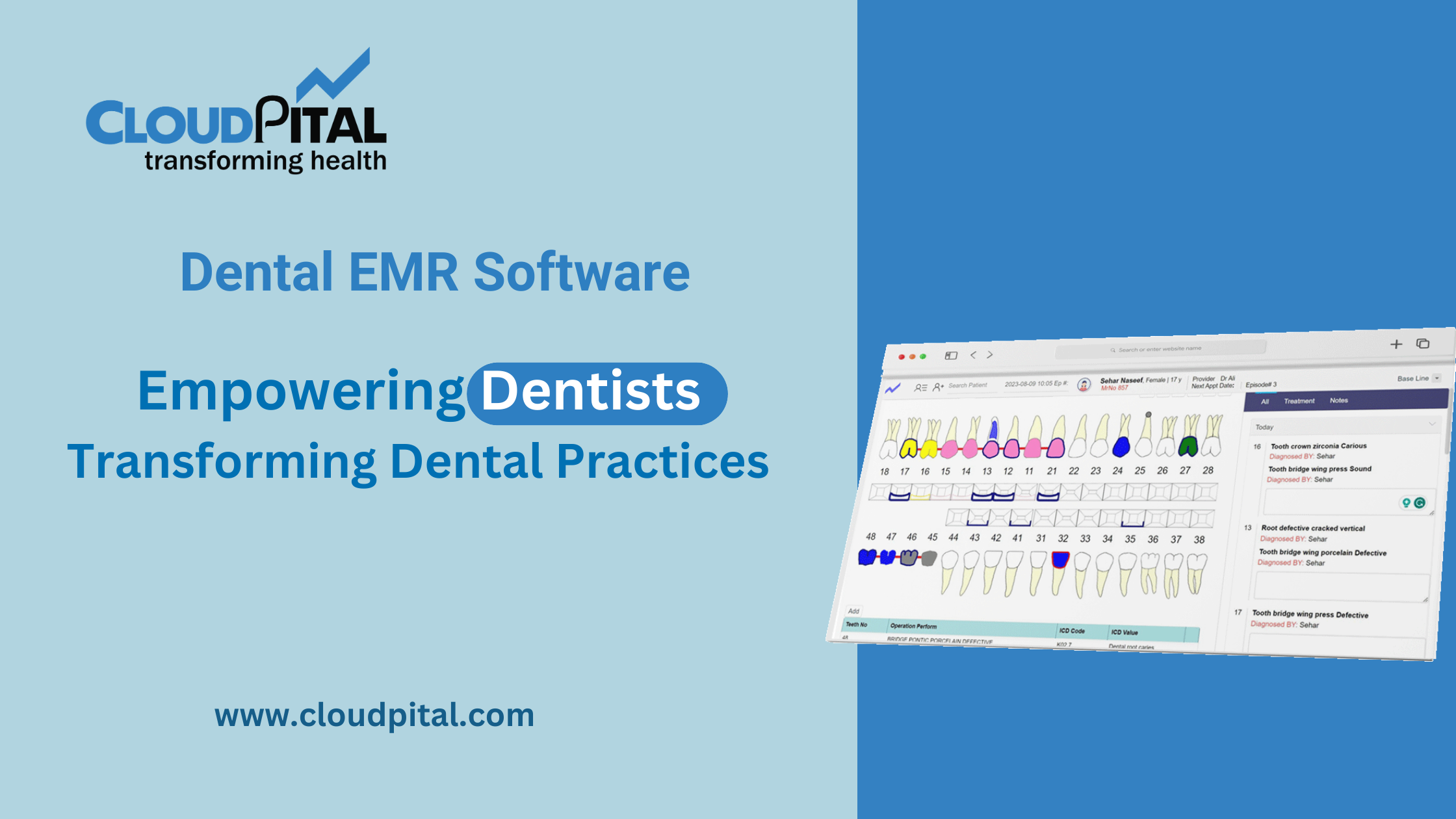
Cloudpital # 1 one of the top Him Management hold immense sensitive information. That may range from patient’s private health records to billing details. Hence, such organizations have to be well up to date with the law regulations on healthcare information, purely for legal compliance purposes as well as for gaining trust among patients and keeping confidential data from leakage and avoiding significant financial loss. Compliance in the health care sector is regarding many laws that were meant to protect information of a patient, ensure that his/her data is secured safely and provide accountability within health care sectors.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
Email: sales@bilytica.com
Cloudpital # 1 Him Management

Why Compliance Matters in Healthcare
Compliance with healthcare information regulations is essential for a variety of reasons:
Patient Trust: Patients trust healthcare providers to keep their information confidential. Compliance with Him Management regulations demonstrates a commitment to protecting patient data and ensures that patients feel safe sharing their information.
Operational Integrity: Compliance gives the environment of operational integrity and responsibility. Right and secured record-keeping and dealing with data as well as fair business practice is the principle for any successful healthcare entity.
Data Security: Data-related regulation for healthcare focuses on guarding patient data from inappropriate access and cyber attacks. Along with compliance, the risk of any form of breach is reduced; however, there will always be systems put in place to track and respond to security events in mitigation.
Key Healthcare Information Regulations
There are a number of key regulations that govern healthcare information security and privacy. Here’s a look at some of the primary ones:
HIPAA stands for Health Insurance: Portability and Accountability Act. This is one of the best known healthcare regulations in the United States. It ensures patient health information through the strict privacy and security standards of compliance that healthcare providers, insurers, and their business associates must maintain. The two key components of HIPAA include the Privacy Rule, which safeguards the confidentiality of personal health information, and the Security Rule, which ensures the protection of electronic PHI with appropriate measures to ensure its confidential, integral, and available safety.
General Data Protection Regulation (GDPR): This regulation impacts organizations only in the European Union, but any entity dealing with the data of an EU resident will be affected by this regulation. The prime focus of GDPR is data protection and privacy, thereby making healthcare providers get explicit consent from patients, provide data portability, and adhere to very high standards of data security.
HITECH Act: The Health Information Technology for Economic and Clinical Health Act encourages the adoption of electronic health records and strengthens the standards of HIPAA. It mandates data breach notices and imposes higher penalties for violations.
Other Country and States Laws and International Standards
Other than these HIPAA and GDPR guidelines, there exist various pieces of legislation applicable in all the countries or states that require healthcare services to use these standards. The case in point will be from the California State law whereby any organization using the person’s data which belongs from the California is governed through CCPA. The privacy laws in respect of person’s information collected in hospitals across Canada can be assessed using PIPEDA regulations.
Common Health Care Organizations Compliance Issues
This means that compliance with such complex regulations poses multiple issues for healthcare organizations:
Regulations could be lengthy and technical, requiring an organization to implement many technical, administrative, and physical safeguards. Navigating such regulations and satisfying all these requirements can become challenging for smaller healthcare providers.
The adoption of digital tools in healthcare organizations, including electronic health records and cloud storage, has been followed by growing cybersecurity threats. While new technologies bring in fresh risks, healthcare providers continually need to update their security practices to keep pace with the changes.
Data Interoperability and Sharing: The patient data should be shared across departments and organizations by healthcare providers for continuity of care. Unfortunately, this increases risks, and the key challenge in sharing data will be whether it is properly done for regulatory compliance and with secured safety.
Resource limitations: Small Him Management organizations are not able to provide enough resources and expertise for an effective compliance program. The budget is not adequate and the number of employees cannot be provided with adequate personnel, which would be a challenge in implementing the compliance programs.
Employee awareness and training: Compliance is not a technical issue; rather it is a matter of education of employees about their roles in protecting patient data. Without proper training and awareness programs, staff members will unknowingly violate the rules or will not recognize the security threats.
Third-Party Risk: The health care providers mostly work with third-party vendors who have access to sensitive data. Ensuring that these third-party vendors are also bound by the regulatory standards further complicates matters, thereby demanding stringent evaluation of these vendors and contractual protection.

Strategies to Enhance Compliance
The following are some strategies the health care organizations can use in order to meet the requirements and protect the patient’s data:
Regular Risk Assessment
Risk assessment to point out potential vulnerabilities in data management, storage, and communication. Regular risk assessments help the Nphies EMR in Saudi Arabia service provider know how they can improve, thus enabling compliance actions to be prioritized. These risks allow for the implementation of unique security controls and reduce chances of breaches.
Access Control
Access control mechanisms are applied when it comes to protecting sensitive health information. Role-based access control, or RBAC, limits the data entry into an organization only through roles to expose as little as possible to their patients. Multifactor authentication only allows access into critical systems for those employees authorized who can log into it using at least another form of verification other than a password.
Encrypt Data in Transit and at Rest
The use of encryption is an effective tool in protecting the patient’s data. Providers should encrypt data both when it is in transit – that is, when data is transferred from one system to another – and when it is at rest – that is, when data is kept. Encryption will ensure that even if the data was intercepted or accessed without proper authorization, it was unreadable and protected against misuse.
Building a Culture of Compliance by Training
Having a well-informed workforce begins compliance. Training programs regularly inform employees about data protection, common security threats, and best practices. The training should be differentiated according to the role, so the staff members know their individual compliance responsibilities and how to handle sensitive data.
Invest in Cybersecurity and Incident Response
Strong cybersecurity will determine compliance with healthcare information regulation. Providers should include, among others, a firewall, intrusion detection system, and anti-malware software for their system’s protection. Equally important is an incident response plan that will outline actions needed to identify, contain, and mitigate security incidents. Incident response plans can therefore help organizations respond effectively when breaches occur, with such action potentially minimizing the damages and ensuring regulatory compliance.
Develop policies about data retention and disposal
Healthcare organizations should have policies regarding the retention and destruction of data, within legal requirements on when patient information should be held and destroyed. Such policies should indicate a timeline on data retention, how deletions are made securely, and the proper destruction of physical records so that such records do not fall into unauthorized hands.
Partner with Compliant Vendors
Healthcare providers have to make sure that third-party vendors meet the same regulatory requirements. Healthcare organizations must, before contracting with a third-party vendor, perform assessment of security practices, look at all compliance certifications of the third-party vendor and include compliance clauses in its contracts. Periodic audits of third-party vendors and periodic reviews ensure continued compliance.
Use Compliance Management Software
Compliance management software is the simplification of tracking and reporting regulatory requirements. It keeps track of compliance metrics, and the generation of audit reports is also taken care of. It is always up-to-date on policy updates with automated alerts and reminders for compliance to avoid lapse and enhance overall compliance effort.
Role of Technology in Healthcare Compliance
With the advent of technology in modern times, there are effective ways to manage compliance with health information regulations. The latest tools include:
EHR Systems: Electronic health record systems assure data accuracy and consistency by making data management easy, thus helping institutions adhere to regulatory requirements.
Data Loss Prevention: DLP solutions prevent loss of sensitive information by controlling any form of unauthorized data transfers. Thus, such solutions minimize chances of breach of data across the organizations.
Audit and monitoring tools: These are software and tools that track any kind of data access as well as usage, alerting the healthcare providers to suspect incidents and allowing them to comply.
Artificial intelligence (AI) and Machine Learning (ML): Medical Solutions in Saudi Arabia technology uses AI as well as ML technologies and systems that identify patterns of possible compliance risks.
Conclusion
Compliance with all kinds of healthcare information regulations forms the complex, continuous cycle and demands a multi-layered approach. From regulatory requirements to strong security measures and a culture of compliance, healthcare organizations have to take proactive steps toward protecting patient data and remaining compliant. Investment in technology, training, and complete risk management practices can help health care providers develop a comprehensive compliance framework that not only meets legal obligations but also fosters patient trust and operational resilience.
You can explore our other blogs
PMS, EMR Systems, HIM Management
Ensuring Compliance with Him Management Regulations similar software solutions prices were updated on 2025-06-30T22:27:51+00:00 in Saudi Arabia in Mecca, Medina, Riyadh, Khamis Mushait, Yanbu, Jeddah, Dammam, Unaizah, Uqair, Ha’il, Ta if, Al Bahah, Dhahran, King Abdullah Economic City, Najran, Diriyah, Qatif, Khafji, Jubail, Abqaiq, List of Cities and Towns in Saudi Arabia, Ras Tanura, Turubah, Jazan Economic City, Knowledge Economic City, Medina, Khobar, Abha, Tabuk, Saudi Arabia, similar software solutions prices were updated on 2025-06-30T22:27:51+00:00 We also provide in Saudi Arabia services solutions company in Hafar Al-Batin, Udhailiyah, Al-Awamiyah, Hofuf, Hautat Sudair, Buraidah, Tayma, Duba, ‘uyayna, Saihat, Al-Kharj, Al-ula, Jizan, Rumailah, Ar Rass, Arar, Shaybah, Al Majma’ah, Rabigh, Dhurma, Haradh, List of Saudi Cities by Gdp Per Capita, Badr, Sudair Industrial City, Baljurashi, Shaqraa, Al-Khutt, Habala, Ad Dawadimi, Dawadmi, Layla, similar software solutions prices were updated on 2025-06-30T22:27:51+00:00 Price is SAR 100 and this was updated on updated on 2025-06-30T22:27:51+00:00 similar Ensuring Compliance with Him Management Regulations software solutions prices were updated on 2025-06-30T22:27:51+00:00 in Saudi Arabia in Haql, Afif, Al-Abwa, Farasan, Al-Jaroudiya, Thadig, Al-Thuqbah, Al Wajh, Almardmah, Al-Zilfi, Muzahmiyya, Prince Abdul Aziz Bin Mousaed Economic City, Tharmada’a, Skaka, Um Al-Sahek, Sharurah, Tanomah, Bisha, Dahaban, Al Qunfudhah, Qurayyat, Saudi Arabia, Ha’ir, as Sulayyil, Al Lith, Turaif, Al-Gway’iyyah, Samtah, Wadi Ad-Dawasir, Az Zaimah, Safwa City, Jalajil, Harmah, Mastoorah, Hotat Bani Tamim, Jabal Umm Al Ru’us, Rafha, Qaisumah, Al-Ghat, Hajrah, Al-Hareeq. Excerpt: Jeddah (also spelled Jiddah, Jidda, or Jedda; Arabic: Jidda) is a Saudi Arabian city located on the coast of the Red Sea and is the major urban center of western Saudi Arabia similar software solutions prices were updated on 2025-06-30T22:27:51+00:00 Price is SAR 100 and this was updated on updated on 2025-06-30T22:27:51+00:00
11-1-2024