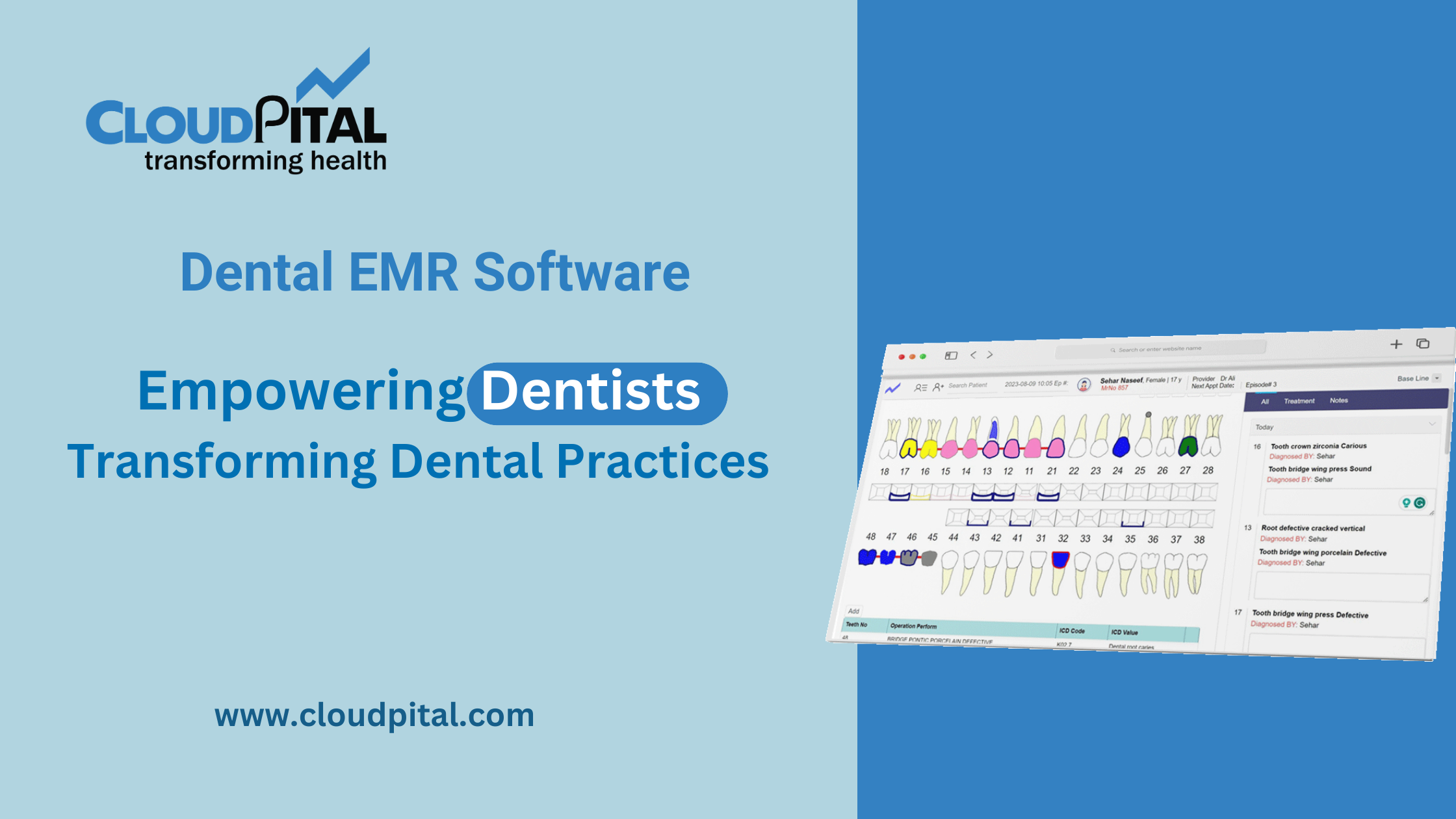
Cloudpital # 1 is one of the top EMR has become a necessity for medical professionals globally. By providing a platform to centralize patient data, automate workflows, and enhance communication, EMR software has transformed patient care. Yet, since patient information is extremely personal and sensitive, one of the biggest concerns regarding the implementation of EMR software is maintaining strong data security. Data breaches, hacking attacks, and unauthorized access are all dangers that can invade the privacy of patients and the integrity of healthcare organizations.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
Email: sales@bilytica.com
Cloudpital # 1 EMR

Encryption and Secure Data Storage
Encryption is one of the major means by which EMR software protects data from security breaches. Encryption is the process of encoding data so that it is readable and accessible only through the use of a decryption key. EMR systems employ encryption algorithms to secure patient data when stored in the system and during transfer.
Once data is housed in an EMR system, it is secured by being encrypted, so even if a cyber attacker can break into the database, the data will be impossible to read without the proper decryption key. This is an additional layer of defense against improper access and guards against data theft.
Access Control and User Authentication
EMR systems come equipped with advanced mechanisms of access control to ensure that only the authorized staff members have access to patient information. Access control enables healthcare organizations to restrict who can read, update, or erase sensitive data according to their job roles and responsibilities within the organization.
For instance, physicians, nurses, and administrative personnel can have varying levels of access to the EMR system based on their position. A physician can have unrestricted access to a patient’s health records, while administrative personnel might only have access to billing and scheduling details. This least privilege principle makes sure that patient information is not exposed to individuals who do not need it in order to carry out their functions.
Audit Trails and Monitoring
EMR systems have extensive audit trails that track each action performed in the system, including who viewed patient information, when it was viewed, and what was changed. The audit logs are key to monitoring the activity of users and upholding accountability. If there is ever suspected breach or unauthorized view of patient information, healthcare clinicians can use the audit trail to trace back what occurred and determine who was responsible.
Audit trails also make it possible to have an open record of all accesses to patient data, which would be essential for both internal examination as well as external regulatory audits. The logs may assist healthcare organizations with ensuring that their EMR system is utilized appropriately and as per security policy and regulation.
Regulatory Standards Compliance
Another significant method by which EMR software facilitates data security is through its compliance with regulatory guidelines. Healthcare practitioners have an obligation to safeguard patient information under various regulations and legislations, such as the Health Insurance Portability and Accountability Act (HIPAA) in America, the General Data Protection Regulation (GDPR) in Europe, and other data protection acts across the globe.
HIPAA, for example, imposes rigid standards on how patients’ information is safeguarded, including encryption requirements, access controls, audit logs, and secure connections. EMR systems that are HIPAA-compliant adhere to these standards so that sensitive patient information can be safeguarded at all times.

Backup and Disaster Recovery
HIMS Software ensures strong security capabilities, yet data can be at risk from catastrophes in the form of natural disasters, system crashes, or hacking attacks. To provide protection against loss of data, EMR systems tend to feature automatic backup and disaster recovery functionalities.
Backing up data guarantees that a duplicate of all patient files is kept in an independent, secure location. This guarantees that, in the case of system failure or cyber attack, patient data is able to be restored without loss from the backup immediately. Most EMR systems utilize cloud-based storage, enabling safe, off-site backup accessible even if physical servers are lost.
Data Anonymization and De-Identification
In some instances, medical personnel can have to utilize patient information for analysis or research. But they must preserve patient privacy when they use the information for purposes outside of immediate care of the patient.
EMR software facilitates data protection by providing options like data anonymization and de-identification. Anonymization deletes all personal identifiers from the patient’s data, and de-identification substitutes identifying information with codes or pseudonyms. By doing this, patient data can be utilized by healthcare organizations for research, population studies, or quality improvement efforts while maintaining the confidentiality of the patient.
Security Patches and Updates
Cybersecurity is a dynamic field, and EMR software companies regularly issue security patches and software updates to patch newly identified vulnerabilities. The updates can resolve security vulnerabilities, introduce new functionality, and make the EMR system immune to recent cyber threats.
Regular patching is important to ensure data security since older software is more prone to hacking and breaches. EMR software vendors tend to provide automated updates to ensure healthcare organizations are compliant with current security standards without the need for manual intervention.
Role-Based Security Settings
Role-based security controls enable healthcare organizations to determine which people are authorized to see particular information according to their role within the organization. For example, a doctor can have access to a patient’s entire medical record, but a nurse would be able to see only vital signs and medication orders.
Role-based access ensures that sensitive information is available only to those who require it to carry out their responsibilities. By restricting access to patient information according to roles, Mobile EHR providers can limit the possibility of unauthorized access and lower the likelihood of data breaches.
Conclusion
EMR software also has a central role in providing security for confidential patient information, and it implements a number of strong features that protect the information. By applying encryption, access control, authentication of users, and audit trails, EMR systems offer security layers against intrusion and data theft. Adhering to regulation standards, such as HIPAA and GDPR, guarantees that health providers are abiding by legal standards for information protection.
Additionally, feature-rich functions such as backup and disaster recovery, data anonymization, and timely software updates ensure that patient information is even better secured. These security features empower EMR software to not just safeguard sensitive details but also provide confidence between providers and patients as medical data keeps being kept in a safe, confidential manner within a rapidly globalizing world.
How does EMR Software help with data security? similar software solutions prices were updated on 2025-06-15T16:15:41+00:00 in Saudi Arabia in Mecca, Medina, Riyadh, Khamis Mushait, Yanbu, Jeddah, Dammam, Unaizah, Uqair, Ha’il, Ta if, Al Bahah, Dhahran, King Abdullah Economic City, Najran, Diriyah, Qatif, Khafji, Jubail, Abqaiq, List of Cities and Towns in Saudi Arabia, Ras Tanura, Turubah, Jazan Economic City, Knowledge Economic City, Medina, Khobar, Abha, Tabuk, Saudi Arabia, similar software solutions prices were updated on 2025-06-15T16:15:41+00:00 We also provide in Saudi Arabia services solutions company in Hafar Al-Batin, Udhailiyah, Al-Awamiyah, Hofuf, Hautat Sudair, Buraidah, Tayma, Duba, ‘uyayna, Saihat, Al-Kharj, Al-ula, Jizan, Rumailah, Ar Rass, Arar, Shaybah, Al Majma’ah, Rabigh, Dhurma, Haradh, List of Saudi Cities by Gdp Per Capita, Badr, Sudair Industrial City, Baljurashi, Shaqraa, Al-Khutt, Habala, Ad Dawadimi, Dawadmi, Layla, similar software solutions prices were updated on 2025-06-15T16:15:41+00:00 Price is SAR 100 and this was updated on updated on 2025-06-15T16:15:41+00:00 similar How does EMR Software help with data security? software solutions prices were updated on 2025-06-15T16:15:41+00:00 in Saudi Arabia in Haql, Afif, Al-Abwa, Farasan, Al-Jaroudiya, Thadig, Al-Thuqbah, Al Wajh, Almardmah, Al-Zilfi, Muzahmiyya, Prince Abdul Aziz Bin Mousaed Economic City, Tharmada’a, Skaka, Um Al-Sahek, Sharurah, Tanomah, Bisha, Dahaban, Al Qunfudhah, Qurayyat, Saudi Arabia, Ha’ir, as Sulayyil, Al Lith, Turaif, Al-Gway’iyyah, Samtah, Wadi Ad-Dawasir, Az Zaimah, Safwa City, Jalajil, Harmah, Mastoorah, Hotat Bani Tamim, Jabal Umm Al Ru’us, Rafha, Qaisumah, Al-Ghat, Hajrah, Al-Hareeq. Excerpt: Jeddah (also spelled Jiddah, Jidda, or Jedda; Arabic: Jidda) is a Saudi Arabian city located on the coast of the Red Sea and is the major urban center of western Saudi Arabia similar software solutions prices were updated on 2025-06-15T16:15:41+00:00 Price is SAR 100 and this was updated on updated on 2025-06-15T16:15:41+00:00