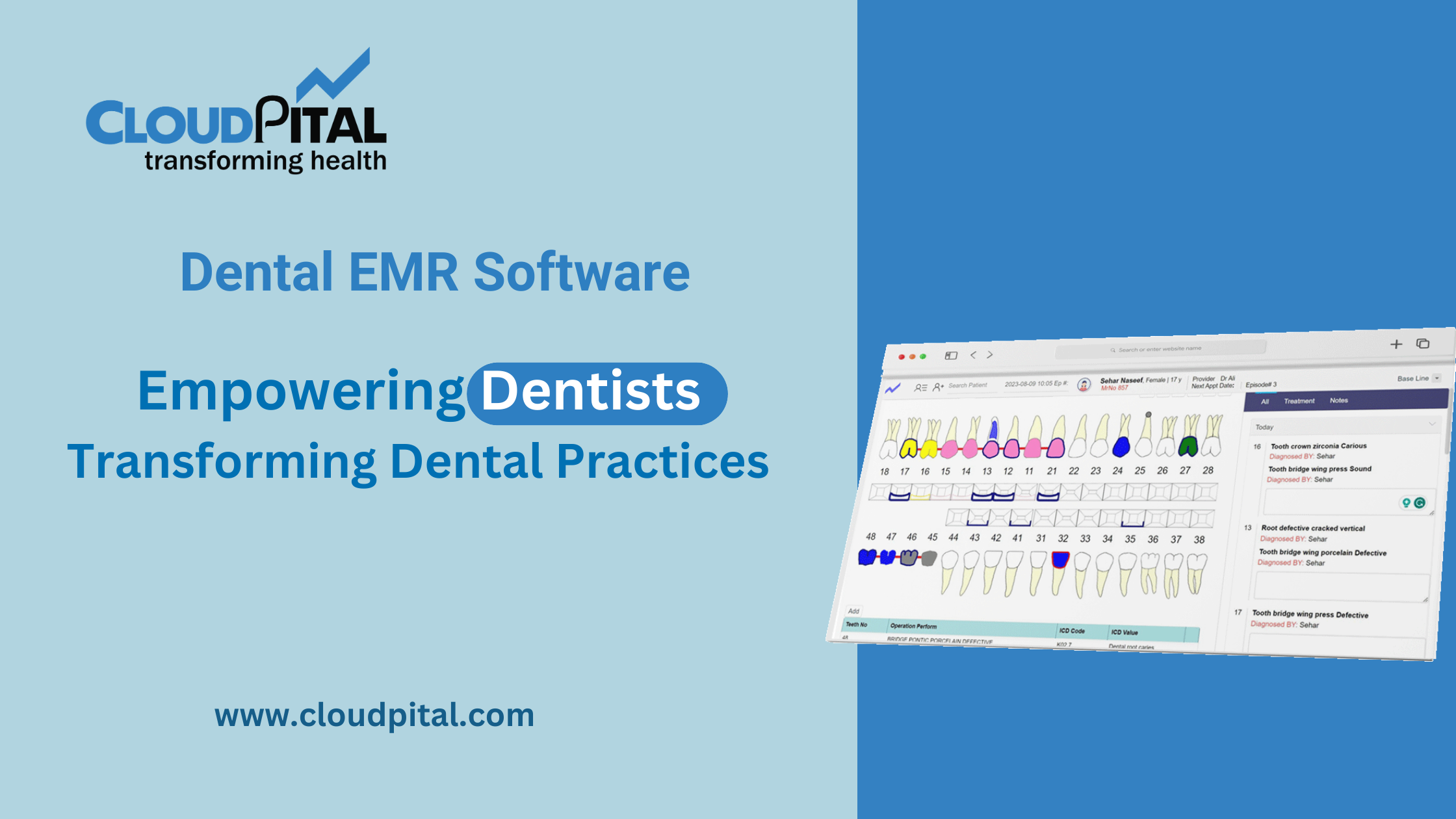
Cloudpital # 1 is one of the top Medical Solutions in Saudi Arabia ensuring data security and patient privacy is paramount in the healthcare sector, and medical solutions are equipped with robust measures to safeguard sensitive information and comply with stringent regulatory requirements. This article delves into the mechanisms and protocols employed by medical solutions to uphold data security and patient privacy in the Kingdom.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
Email: sales@cloudpital.com
Cloudpital # 1 Medical Solutions in Saudi Arabia

Encryption and Secure Transmission
Medical Solutions in Saudi Arabia utilize encryption techniques to protect data both at rest and in transit. Advanced encryption algorithms are employed to encode sensitive information such as patient health records, ensuring that only authorized individuals can access and decipher the data. Secure transmission protocols, such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS), encrypt data as it travels between devices, servers, and networks, preventing unauthorized interception or tampering.
Role-Based Access Control (RBAC)
Role-based access control mechanisms are implemented within medical solutions to regulate user access and permissions based on predefined roles and responsibilities. Each user is assigned a specific role within the system, dictating the level of access they have to patient data and system functionalities. RBAC ensures that only authorized personnel with a legitimate need to access patient information can do so, minimizing the risk of unauthorized data breaches or misuse.
User Authentication and Authorization
Medical solutions employ robust user authentication mechanisms, such as biometric authentication, multi-factor authentication (MFA), and strong password policies, to verify the identity of users and prevent unauthorized access to the system. Upon successful authentication, users are granted appropriate authorization levels based on their role and privileges, ensuring that they can only access data and perform actions relevant to their responsibilities.
Data Encryption at Rest
Sensitive data stored within Medical Solutions in Saudi Arabia including electronic health records (EHRs), diagnostic images, and laboratory results, is encrypted at rest to prevent unauthorized access in the event of a security breach or data theft. Encryption keys are securely managed and stored separately from the encrypted data, adding an additional layer of protection and ensuring that only authorized users with the requisite decryption keys can access the information.

Audit Trails and Logging
RCM maintain comprehensive audit trails and logging mechanisms to track and record all user interactions and system activities. Audit logs capture details such as user logins, access attempts, data modifications, and system configuration changes, providing a detailed record of who accessed what data and when. By monitoring and analyzing audit logs, healthcare organizations can detect suspicious activities, investigate security incidents, and demonstrate compliance with regulatory requirements.
Data Backup and Disaster Recovery
Medical solutions implement robust data backup and disaster recovery strategies to mitigate the risk of data loss due to hardware failures, natural disasters, or cyberattacks. Regularly scheduled backups ensure that critical patient data is replicated and stored securely in off-site locations or cloud-based repositories. In the event of a system outage or data breach, healthcare organizations can restore data from backups and resume operations with minimal disruption.
Regulatory Compliance
Medical solutions adhere to stringent regulatory frameworks and standards to ensure compliance with data protection laws and regulations in Saudi Arabia, such as the Health Insurance Portability and Accountability Act (HIPAA), the Saudi Data and Artificial Intelligence Authority (SDAIA) regulations, and the Saudi Food and Drug Authority (SFDA) guidelines. Compliance with these regulations entails implementing appropriate technical, administrative, and physical safeguards to protect patient data and privacy.
Continuous Monitoring and Security Audits
Medical solutions undergo regular security audits, vulnerability assessments, and penetration testing to identify and address potential security vulnerabilities and weaknesses. Continuous monitoring of system activities and network traffic allows healthcare organizations to detect and respond to security incidents in real-time, minimizing the impact of potential threats and breaches.
Training and Awareness Programs
Healthcare organizations provide comprehensive training and awareness programs to educate employees about the importance of data security and patient privacy. Training sessions cover topics such as security best practices, password hygiene, phishing awareness, and incident response procedures, empowering staff to recognize and mitigate security risks effectively.
Vendor Security Assessments
Before procuring or deploying EHR Systems in Saudi Arabia healthcare organizations conduct thorough security assessments and due diligence on vendors to ensure that their products meet stringent security standards and compliance requirements. Vendor security assessments evaluate factors such as data encryption protocols, access controls, security certifications, and adherence to regulatory frameworks.
Conclusion
Medical solutions play a critical role in safeguarding patient data and privacy in Saudi Arabia, employing a comprehensive array of technical, administrative, and organizational measures to mitigate security risks and ensure compliance with regulatory requirements. By implementing robust encryption, access controls, audit trails, and security protocols, healthcare organizations can protect sensitive information and maintain patient trust in the confidentiality and integrity of their healthcare data.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
Email: sales@cloudpital.com
Medical Solutions in Saudi Arabia
Medical Solutions in Saudi Arabia
Medical Solutions in Saudi Arabia
Medical Solutions in Saudi Arabia ensure data security similar software solutions prices were updated on 2025-06-16T03:40:38+00:00 in Saudi Arabia in Mecca, Medina, Riyadh, Khamis Mushait, Yanbu, Jeddah, Dammam, Unaizah, Uqair, Ha’il, Ta if, Al Bahah, Dhahran, King Abdullah Economic City, Najran, Diriyah, Qatif, Khafji, Jubail, Abqaiq, List of Cities and Towns in Saudi Arabia, Ras Tanura, Turubah, Jazan Economic City, Knowledge Economic City, Medina, Khobar, Abha, Tabuk, Saudi Arabia, similar software solutions prices were updated on 2025-06-16T03:40:38+00:00 We also provide in Saudi Arabia services solutions company in Hafar Al-Batin, Udhailiyah, Al-Awamiyah, Hofuf, Hautat Sudair, Buraidah, Tayma, Duba, ‘uyayna, Saihat, Al-Kharj, Al-ula, Jizan, Rumailah, Ar Rass, Arar, Shaybah, Al Majma’ah, Rabigh, Dhurma, Haradh, List of Saudi Cities by Gdp Per Capita, Badr, Sudair Industrial City, Baljurashi, Shaqraa, Al-Khutt, Habala, Ad Dawadimi, Dawadmi, Layla, similar software solutions prices were updated on 2025-06-16T03:40:38+00:00 Price is SAR 100 and this was updated on updated on 2025-06-16T03:40:38+00:00 similar Medical Solutions in Saudi Arabia ensure data security software solutions prices were updated on 2025-06-16T03:40:38+00:00 in Saudi Arabia in Haql, Afif, Al-Abwa, Farasan, Al-Jaroudiya, Thadig, Al-Thuqbah, Al Wajh, Almardmah, Al-Zilfi, Muzahmiyya, Prince Abdul Aziz Bin Mousaed Economic City, Tharmada’a, Skaka, Um Al-Sahek, Sharurah, Tanomah, Bisha, Dahaban, Al Qunfudhah, Qurayyat, Saudi Arabia, Ha’ir, as Sulayyil, Al Lith, Turaif, Al-Gway’iyyah, Samtah, Wadi Ad-Dawasir, Az Zaimah, Safwa City, Jalajil, Harmah, Mastoorah, Hotat Bani Tamim, Jabal Umm Al Ru’us, Rafha, Qaisumah, Al-Ghat, Hajrah, Al-Hareeq. Excerpt: Jeddah (also spelled Jiddah, Jidda, or Jedda; Arabic: Jidda) is a Saudi Arabian city located on the coast of the Red Sea and is the major urban center of western Saudi Arabia similar software solutions prices were updated on 2025-06-16T03:40:38+00:00 Price is SAR 100 and this was updated on updated on 2025-06-16T03:40:38+00:00
6-12-2024